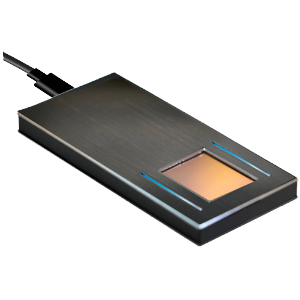
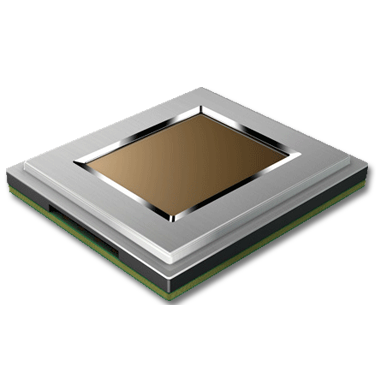
HID® TouchChip™ TCET Module on-board processor is used for Mobile ID Terminals, Single Sign-on, Time and Attendance, Point of Sale Security, Patient ID

TouchChip TCET Module Details
Easy to integrate
The HID® TouchChip™ TCET Module is compact, cost effective and easy to integrate.
The on-board processor is used for capture and match, delivering fast and accurate results.
It can store up to approximately 100 user templates and supports USB, SPI or UART interfaces.
Power consumption is less than 100mA during capture and match.
For easy integration, the TCET module is fully assembled and tested — just connect and interface using simple commands.
The Enhanced Image Mode (EIM) optimizes image quality over a broad range of skin types and capture conditions.
The TCET module eliminates latent images during capture and offers ingress protection from dust and moisture penetration to IP65.
TouchChip TCET Module is Used for Mobile ID Terminals, Single Sign-on, Time and Attendance, Point of Sale Security, Patient ID
Supports WSQ and JPEG2000
The module supports WSQ and JPEG2000 compression with the appropriate Software Development Kit (SDK).
The TouchChip TCET module includes broad software support from leading algorithm providers, ISV’s and system integrators.
Whether you are an OEM or system integrator, HID’s biometric identity verification solutions provide a natural extension to your applications.
ESSENTIAL CONDITIONS OF HID® FINGERPRINT READER
BIOMETRICS INCLUDE FINGERPRINT READERS.
Fingerprint readers are used to securely verify identity
HID covers a wide range of products from the simplest for authentication on PC, network to the most complex of the LUMIDIGM series used by the FBI
CAPTURE
The fingerprint scanner scans your fingerprint.
It can be used for many applications, including access control, license verification, criminal background checks, computer logon, etc.
LIVENESS
Verification of the “liveliness” of a person, in practice verifying that the fingerprint is not a fake, which is performed via a computer system.
This control is usually used to counter fraud and identity theft.
MATCHING
The main categories of fingerprint matching techniques are minutiae-based matching and pattern matching.
Pattern matching simply compares stored images to see how similar they are.
Pattern matching is usually used in fingerprint systems to detect any duplicates.
LEARN MORE
See the document Powering Trusted Identities with Fingerprint Biometrics Brochure
APPLICATIONS
Civil ID/Voting/Benefits Distribution
Logical & Physical Access Control
Mobile ID Terminals
Single Sign-on
Time and Attendance
Point of Sale Security
Patient ID
Key Features
- Steelcoat®: Highest-durability or GoldCoat: FIPS 201 PIV certified
- Low power consumption
- Compact size
- IP65-rated top surface sealed against dust and liquid
- OS: Windows® 7, 8 and 10, Win CE, Linux®, Android™ and embedded systems (with or without OS)